Penetration testing also known as Pen testing intends to detect holes in the system and helps in making sure that the appropriate security measures are in place to secure data and ensure functionality.
Learn Penetration Testing
Since it is crucial for the Software testers, we covered everything needed for them to learn. We’ve prepared this tutorial so that they can understand the basics of Penetration Testing and know how to use it at work.
Here, you’ll get to know, “What is Pen Testing?“, “Why is it required?“, “What are its different types?” along with its benefits and limitations. So let’s dive in further to learn the core concepts of Penetration Testing.
What is Penetration Testing?
Penetration testing is a type of black box testing approach that proposes to make authorized attempts to violate the security and integrity of a system, application, network, or database. It aims to discover and document all the security holes in a system that is likely to compromise it before the hackers.
Although, it has many names, “Pen Testing” is amongst the most popular ones. Its goal is to outsmart the hackers by exposing the weak links or security gaps inside a system. Also, the person who runs a penetration test is called a penetration tester or pentester.
Alternatively, you may classify it as a type of security testing that regresses the weak areas of the system or application. It aims to identify the security vulnerabilities in the target system.
Also Read: Five Areas to Target for Effective Pen Testing
Phases of a Penetration Test
The tests which are part of the Pen testing are known as Penetration tests. Each such test includes the following five stages. Please see the below diagram for clarity.
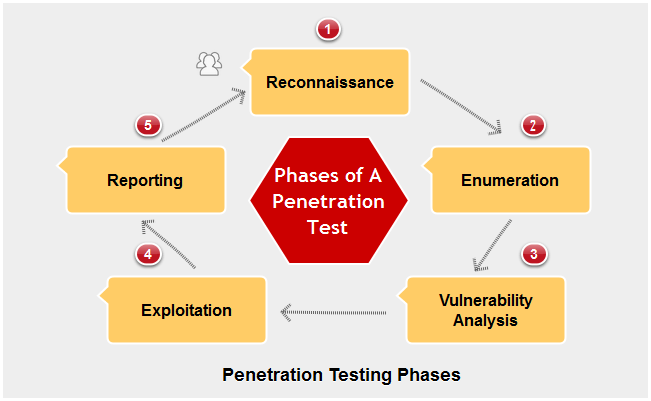
- Reconnaissance – Scout out the target system before striking.
- Enumeration – It involves pinpointing potential access points within the target system.
- Vulnerability Analysis – Assess and classify the target system’s security weaknesses.
- Exploitation – Exploit the target system’s vulnerabilities to gain access.
- Reporting – Document the attack steps and findings.
Also, let’s now review a few of the leading pen testing parameters that you should know.
What is a security weakness or vulnerability?
A vulnerability refers to a security weakness in software, hardware, or an operating system that renders a system susceptible to attacks. This vulnerability can vary from something as simple as a password that’s easy to guess to more complex issues like buffer overflows or tampering with data using SQL injection.
What is an exploit?
An exploit is a software program or a service designed to turn a vulnerability into an opportunity to gain unauthorized entry. It enables hacker access to the target system. Most exploits form a payload to penetrate the target system and grant access to the intruder.
What is a payload?
A payload is a malicious code that, in conjunction with an exploit, grants unauthorized access to a computer system.
It masks the system, either by concealing its true nature or by presenting a deceptive facade, but it then unpacks itself to initiate the attack.
Metasploit is the boss in the field of penetration testing. It makes use of a payload known as a Meterpreter. Once this payload infects the system, it can unleash an array of actions, such as file upload/download, screen capture, and the extraction of password hashes. Ultimately, It leaves you with full control over the infected system.
Why is it essential to conduct Pen Testing?
Pen testing helps you check your system’s security against both internal and outside threats. It finds weaknesses that attackers could exploit and helps you fix them before it’s too late.
Here are a few reasons why pen testing is important:
- It helps you identify and fix security weaknesses before attackers find them.
- It helps you understand how your applications could be attacked.
- It helps you prevent data breaches and revenue loss.
- It helps you make informed decisions about improving your security posture.
In other words, pen testing helps you keep your system safe and sound.
What types of software tests do we do for Pen testing?
We can bifurcate Penetration testing into three categories: black box, white box, and gray box.
Black Box Testing
Since it’s impractical for a hacker to know the exact topology of company infrastructure, launching an all-out, brute force attack is the best odd he or she could try to find out possible vulnerabilities in a system.
Similarly, in this type of penetration test, the tester doesn’t know the internals of a web application. He doesn’t even have any clue about the source code or the system design. Hence, this type of testing may take longer than the expected time to complete.
However, with automation, he can reduce the overhead a bit and focus on uncovering the weaknesses and vulnerabilities. “Trial and Error” is also another popular name for this type of approach.
Black-Box Pros
- It requires little details before commencing.
- Execution behavior is similar to a real attacker. So, there is a high probability of finding real issues.
Black-Box Cons
- A tester won’t have the same time as a real attacker could have for planning the attack
- It would not cover all aspects
- Execution would lead to a high cost
- Not a tool for PCI compliance
White Box Testing
White box assumes that the tester would have in-depth knowledge of the application code and its architecture. And since he is aware of the ins and outs of the application, he can execute it quicker than the black box testing. Alternatively, the test would also be much more comprehensive.
With this type of testing, it is easier to design test cases for penetration testing.
However, it would pose a few challenges which you must address as a tester. For example, the detailed system knowledge could be a constraint in deciding upon the area or component to focus on running the tests and analysis. Also, the testing would need the use of advanced tools like static code analyzers, debuggers, and network sniffers.
White-Box Pros
- It is far more accurate and detailed than the black box approach.
- Planning in this approach is easy. And execution is faster.
White-Box Cons
- Significant time would be required to understand the system and prepare the data for analysis.
- Advanced tool execution would result in cost escalation.
Gray Box Testing
It is a mixture of both the black box and white box testing techniques. Also, in this type of testing, the tester needs just a high-level knowledge of the internals of the Web applications. It is because even this limited knowledge is sufficient for him to gain access to the source code and the system design.
The gray box approach promotes the use of both manual and automated testing. Also, during the execution, the pen tester can first pick on the known application areas. It will make him concentrate on exploiting the existing vulnerabilities. Hence, the gray box testing assures of locating even hard-to-find security leaks.
Gray-Box Pros
- Low cost as compared to other types of testing.
- The pen tester can achieve the same level of coverage as they would have seen during the white box testing.
Gray-Box Cons
- Dependency on the customer to furnish information for pen testing to begin.
Summary – Penetration Testing Or Pen Testing
Being a tester, it is your responsibility to produce error-free software artifacts. Hence, you must know about all the cornerstone concepts in software testing like Penetration testing.
Hopefully, with this tutorial, you will be able to grow your knowledge of this subject.
However, if you have any questions or queries for us, then use our contact page.
Happy Learning,
TechBeamers








